...
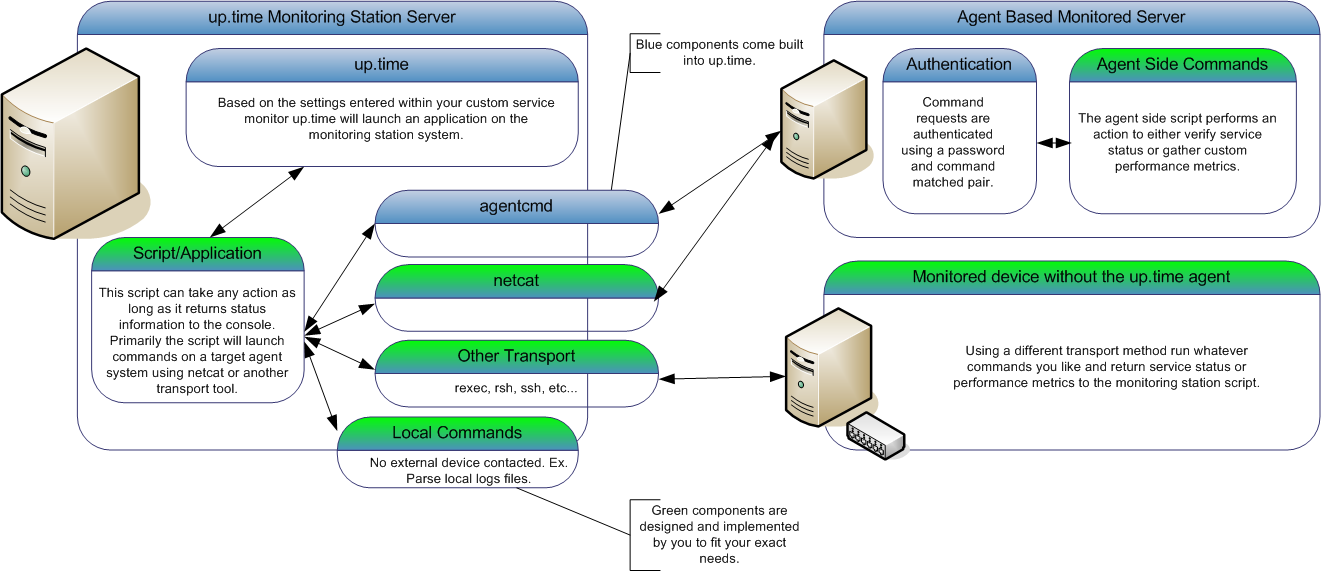
The built-in agent authentication protocol provides a quick and easy way for you to have the up.time agent run commands (or any application) on your agent-side system without the fear of unknown users being able to execute the same commands. The output from the agent-side commands will be returned to the monitoring station custom script for parsing. This enables you to create a script that can monitor many different agent systems without duplicating the script many times. The following diagram illustrates the custom service monitor process:
...
Step 1 - Creating the Agent Side Script
When designing a custom service monitor, you should consider what information that you want the monitor to collect. For example:
...
| Note | ||
|---|---|---|
| ||
| These example commands are formatted for non-Windows systems. The command format is very similar on Windows systems, but require minor syntax and path changes. |
| Code Block | ||
|---|---|---|
| ||
# su - uptime |
...
$ /opt/uptime-agent/my-scripts/show_temp.sh |
...
temp 74 |
...
rh 30 |
To define your password and command pair on a non-Windows agent system, do the following:
- Ensure that a file named .uptmpasswd is created in the up.time agent bin directory -- either /opt/SPYNuptm/bin/ or /opt/uptime-agent/bin, depending the version of your agent. This file must be owned and readable by the user that the agent is run as (ex. uptimeagent or uptime users).
- Open the file .uptmpasswd in a text editor.
- Enter a password and command pair for each command that you want to run on the agent system. The following is the example format and an example of a agent-side commands:
Format:
[password] [command path, no arguments]Example file contents:
Code Block language powershell secretpassword /opt/uptime-agent/my-scripts/show_temp.sh
$%^& /usr/local/bin/appstatus.sh
Windows agents do not require a password file. However, you must enter the equivalent settings into the Agent Console with the following steps:
...
| Note | ||
|---|---|---|
| ||
| If any changes are made to the Windows agent registry please restart the "up.time agent" service to see these changes take effect. |
| Code Block | ||
|---|---|---|
| ||
[HKEY_LOCAL_MACHINE\SOFTWARE\uptime software\up.time agent] |
...
"CmdsTimeout"=dword:00000014 |
...
"Port"=dword:0000270e |
...
"MaxClients"=dword:00000005 |
...
"Debug"=dword:00000000 |
...
"CmdsPassword"="secretpassword" |
...
"LogFile"="log.txt" |
...
[HKEY_LOCAL_MACHINE\SOFTWARE\uptime software\up.time agent\rexec_commands] |
...
"dir"= cmd.exe /c "dir c:" |
...
"show-temp"= cmd.exe /c "C:\scripts\show_temp.pl" |
...
...
Step 2 - Creating the Monitoring Station Script
...
- To get started with custom scripts, or for implementations with only a handful of custom monitor instances, use agentcmd. The agentcmd utility is commonly called in the format listed below to execute a command on the agent side system. Please note that this utility is a helper tool, if you are using many custom monitor instances we recommend using an alternate tool.
This example uses the settings that were configured above to execute the agent side script:Format:
Code Block language text /usr/local/uptime/scripts/agentcmd [-s/+s] -p [agent port] [agent hostname] rexec [password] [path]
Example:Code Block language text /usr/local/uptime/scripts/agentcmd -p 9998 my-agent rexec secretpassword /opt/uptime-agent/my-scripts/show_temp.sh my-arguments
For more information on the syntax used with agentcmd, see this Knowledge Base article.
- If you plan on implementing a number of custom monitor instances, use netcat. netcat must be downloaded and installed on the monitoring station if it isn't already installed as part of your operating system. The netcat utility is commonly called in the format listed below to execute a command on the agent side system. This example uses the settings that were configured above to execute the agent side script:
Format:
Code Block language text echo -n rexec [password] [path] | /usr/local/uptime/bin/netcat [agent hostname] [agent port]
Example:Code Block language text echo -n rexec secretpassword /opt/uptime-agent/my-scripts/show_temp.sh my-arguments | /usr/local/uptime/bin/netcat my-agent 9998
| Note | ||
|---|---|---|
| ||
| The 'rexec' text below does not indicate use of the 'rexec' system utility, it is simply a key word used to indicate to the agent that you are attempting to run a predefined command. |
You will normally use netcat or agentcmd in the monitoring station script to return the results of an agent-side script, validate the status of those results, and return the status to up.time. The following is an example of a monitoring station script:
| Code Block | ||
|---|---|---|
| ||
#!/bin/sh |
...
# This script takes the following arguments: |
...
# check_temp.sh hostname port [temp|rh] wng crit |
...
# Example execution: |
...
# ./check_temp.sh my-agent 9998 temp 60 80 |
...
# ./check_temp.sh my-agent 9998 rh 20 30 |
...
# This script can be placed anywhere on the monitoring station system as long as it is |
...
# executable by the uptime user. |
...
#First, collect our arguments |
...
AGENT=$1 |
...
PORT=$2 |
...
TYPE=$3 |
...
WNG=$4 |
...
CRIT=$5 |
...
TMPFILE=/tmp/$$.temp |
# now use the info above to contact our agent, store the output in a file for parsing
`echo -n rexec secretpassword /opt/uptime-agent/my-scripts/show_temp.sh my-arguments | /usr/local/uptime4/bin/netcat $AGENT $PORT > $TMPFILE`
| Note | ||
|---|---|---|
| ||
| The syntax to use agentcmd is different than netcat. When using agentcmd, the above netcat example would like this: |
...
| Code Block | ||
|---|---|---|
| ||
'/usr/local/uptime/scripts/agentcmd my-agent -p 9998 rexec secretpassword /opt/uptime-agent/my-scripts/show_temp.sh my-arguments > $TMPFILE' |
| Code Block | |
|---|---|
|
...
| |
# we have the output from the agent. If it is ERR that means there was a problem running the script on the agent |
...
`grep ERR $TMPFILE` |
...
if [ $? -eq 0 ] |
...
then |
...
echo "Could not execute agent side script!" |
...
# by exiting with a 2 we are forcing a CRIT service outage |
...
exit 2 |
...
fi
|
| Code Block | ||
|---|---|---|
| ||
# given our parameters we can now extract the correct value from the agent output |
...
if [ $TYPE -eq "temp" ] |
...
then |
...
VALUE=`head -1 $TMPFILE | awk '{print $2}'` |
...
MSG="temperature" |
...
else |
...
VALUE=`tail -1 $TMPFILE | awk '{print $2}'` |
...
MSG="humidity" |
...
fi
|
| Code Block | ||
|---|---|---|
| ||
# now lets check our values to see if they are over the thresholds and set our status message |
...
RET="OK - $msg is $VALUE on $AGENT" |
...
if [ $VALUE -ge "$WNG" ] |
...
then |
...
# this is our warning message |
...
# include WARNING for use in the web interface thresholds |
...
RET="WARNING - $MSG is $VALUE on $AGENT" |
...
fi |
...
if [ $VALUE -ge "$CRIT" ] |
...
then |
...
# this is our critical message |
...
# include CRITICAL for use in the web interface thresholds |
...
echo "CRITICAL - $MSG is $VALUE on $AGENT" |
...
fi |
...
# here we simply print our status message to the console and exit with a 0, |
...
# the thresholds provided in the up.time web interface will be used to set the monitor status |
...
rm $TMPFILE |
...
echo "$RET" |
...
exit 0 |
...
Step 3 - Adding your Custom Service Monitor to up.time
...